1. The DRM problem
The digital age is great for content distribution, be it music, movies, text, or software. The advantages of digital content distribution (DCD) include rapid dissemination on a global scale, cost-effectiveness, unparalleled production capabilities, and highly flexible pricing. However, the ease and convenience of creating, storing, and transmitting data in digital form is a double-edged sword. This stems from the fact that there is no physical real-world substance to human creations anymore: the product of an artist or a software engineer nowadays is merely a sequence of bits that can be perfectly reproduced and even arbitrarily modified by anyone that is experiencing the product in a fully functional local environment.
The ability to reproduce and manipulate content is particularly well suited to large-scale distributed development projects (for instance, Wikipedia or Linux) and it blurs the boundaries between producers, distributors, and consumers of intellectual products. This defies the traditional approach to content dissemination, where such boundaries are much clearer and a content consumer is more restricted (within fair use boundaries) on the ways he or she can manipulate content. (Restriction here should not be understood as putting bounds on the end user, but rather as a way that the content creator can retain certain rights related to how the content is experienced, marketed, distributed, and manipulated.)
This is where the digital rights management (DRM) problem springs up: How is it possible for content producers to mark the boundaries on the ways digital content can be experienced by digital consumers? It is worth noting that the issue of whether such boundaries should exist at all has been put forth. Still, even under the broadest interpretation of fair use, one has to accept that content producers may want to control the ways their products are experienced and marketed. The reasons for this can be quite varied, including enforcement of pricing schemes, arbitrage elimination, artistic integrity, and licensing constraints.
It is instructive to think of content distribution and reproduction as a producer-consumer pairing. Content producers (creators or providers) wish to distribute digital content to consumers, who should access it according to a set of predetermined specifications and rules. Such rules are directly related to the business/distribution model that is pursued by the content provider. This is the setting of the DRM problem. If we find a way to express the specifications of usage that make the producer-consumer pairing viable, and build a distribution system that ensures there is no way to violate them, the problem is solved.
An abstract DCD system is illustrated in Figure 1. In this system, digital content is licensed to be reproduced in a certain way by the consumer, and its ownership is typically not transferred. Take for example the DCD system employed by an online video streaming service. In this particular instantiation of the abstract system of Figure 1, the content providers are the channels that are participating in the service. The distribution channel is the Internet. The distribution/license server is the web server that coordinates the streaming service. The reproduction device is a video player running locally on the consumer side.
| | 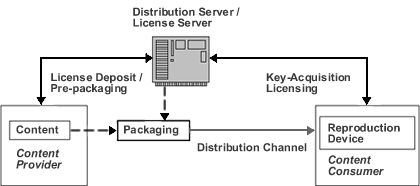
Figure 1: An abstract digital content distribution (DCD) system overview: the content provider stores a license and perhaps prepackages the content with a server. Subsequently, the content is packaged and distributed to consumers. Consumers activate or obtain their licenses and keys from the server, either ahead of content delivery or upon delivery. Then, they unpackage the content (using the keys), and access it using a suitable reproduction device.
| |
The distribution of movies on DVD can also be described by the model in Figure 1. In this case, the content providers are the companies that have purchased the right to distribute movies; the distribution channel is a DVD disk. The reproduction device is any DVD player.
The solution of a computer security problem requires the understanding of possible adversarial behaviors that come in the form of various attacks against the system. One very basic attack on DCD systems is unauthorized content reception, where the adversary consumes content without having the license for it. Another common attack is ownership hijacking, where the adversary takes over the ownership of the digital content and then uses it as his own. A third general attack is unauthorized content redistribution, where the adversary has access to the content legally, but redistributes it to other receivers in license violation.
For example, in the video streaming scenario, unauthorized content reception may refer to the reception of a video stream from the server without performing the required actions (for example, filling out a required form or paying for the stream). In the case of DVDs, unauthorized content redistribution may refer to a situation where the adversary obtains a DVD licensed only for private viewing, rips it in a stream, and uploads it to an online streaming server that is connected to the Internet.
Numerous other types of attacks exist. For example, content may have an expiration date and the adversary may wish to access it beyond that date. More generally, the content is supposed to be accessible only within a certain environment or for a specific subscription type, and the adversary attempts to violate this condition. These attacks should be considered in conjunction with the variety of different types of content distribution, and the various modes of adversarial operation. For example, the adversary could be outside the system, or have various degrees of involvement and proximity to the system's components. The number of possible attacks against a DCD system is therefore as many as the combinations of possible license violations and deployment environments.
2. Cryptography and the DRM problem in the large
Cryptography is an area of computer science that can play a decisive role in solving the DRM problem. In cryptography, an implementation of a system is considered useful if it provides explicit and provable guarantees against specifically defined adversarial behaviors, or attacks. Applying this logic to the DRM problem, cryptographers seek to identify and formalize different types of attacks against a DCD system, and then to provide techniques for constructing systems with provable guarantees against these attacks, under plausible assumptions regarding the system's environment.
Some assumptions that may be employed in a DRM system are purely mathematical -- for example, that finding the factors of certain composite numbers in a reasonable amount of time is impossible. Others have to do with the physical implementation of a system -- for instance, that the system is free of viruses or spyware, or that users do not store their keys in a publicly accessible file.
The goal of cryptography can be seen as minimizing the number of external assumptions that need to be enforced in a system while providing the “glue” that holds together a system's components. Nevertheless, good cryptography alone cannot make a DCD system secure and viable. It will be the duty of those who deploy DCD systems to make sure that the necessary assumptions hold. Therefore, the DRM problem goes beyond cryptography and includes issues in the following three broad categories: system implementation and development; business and economics; and legal, social, and ethical aspects.
Implementation and development issues have to do with the actual materialization of a DCD design into a usable system, for example, the nature of the distribution medium, the hardware and software involved and its correct development, and the human-computer interface. Currently, we are witnessing wide deployment of fully fledged DCD systems, such as Microsoft's Windows Media DRM system and Apple's Fairplay, as well as a number of specialized, but fully functional solutions for specific application settings, such as digital cinema [1].
Turning to the business aspects and trends, as a society we are experiencing the turmoil due to the advent of file-sharing networks. New distribution and marketing models inspired by file sharing for various types of content have been proven successful (for example, the iTunes model) and are serious competitors to traditional distribution methods. At the same time, the entertainment industry has initiated vigorous action to pressure legislators and manufacturers to control the damage since the new technological developments threaten current business models. Still, there are substantial benefits to supporting the new technology, and the industry is willing to sacrifice rights for interoperability and usability as seen in the April 2007 decision of EMI to allow distribution of unprotected music through iTunes. As was the case with the advent of the VCR and previous technological breakthroughs, the digital content markets will move toward new workable equilibria. Today's intellectual property wars and their outcomes will have a deep impact on the way we design DCD systems and the way we consume digital content in the future [2].
On the legal, social, and ethical front, the challenges and the controversy around DRM are also of great magnitude. Legal backup is an important component of current content distribution systems, and this will continue to be the case in the future. The international scope of content distribution presses for global legal coordination, which is a complex issue. Questions of ethics also arise. Is it acceptable to share music or employ the artistic creations of someone else in a new artistic creation? The boundaries of fair use frequently are unclear. In many recent incidents, the industry and end users find themselves in a tug-of-war where either the end users engage in acts that infringe upon the copyrights of others, or the industry's over-protective attitudes toward owned digital content threaten fair use rights.
3. Putting cryptography to work for DRM
Cryptography can be used to tackle the various adversarial actions against DCD systems in several ways. The epicenter of a DCD system is the packaging mechanism that engulfs the content when it is distributed. Among other uses, packaging is usually meant to protect the content from simple eavesdropping. Eavesdropping protection is essential, given that the DCD environment facilitates perfect content reproduction, which in most cases is undesirable (shareware or open source software is an exception to this rule). An encryption system must also be resilient to attacks that go beyond simple eavesdropping, for instance, leakage of decryption keys. This is illustrated by the fiasco of the DVD Content Scrambling System (CSS) [3]. Moreover, the usability of a DCD system is of great importance if it is to be widely accepted and remain secure. For instance, the demolition of CSS can be also attributed to its usability failure in its lack of support for the CSS DVD player software on the Linux platform (something that strongly motivated the hacking of the packaging system). A system that restricts fair use rights in an essential way is bound to fail.
There are two basic cryptographic primitives that promise to be particularly important for DCD systems. Traitor tracing schemes are encryption systems that are capable of providing protection against key leakage. In a traitor tracing scheme, it is guaranteed that the distribution server will be capable of identifying the compromised keys (traitor keys) once some sort of pirate activity is identified. Broadcast encryption schemes, on the other hand, are encryption systems that allow the revocation of keys that have been compromised.
The above primitives can be strengthened further with asymmetric traitor tracing schemes [4], where the traceability mechanism allows for stronger accountability to further discourage key leakage. In such systems, the traceability mechanism goes beyond identification, and provides strong evidence of the implication of traitors in a piracy incident that can even stand as evidence in a court of law that accepts the legality of digital signatures. The traceability mechanism can be further strengthened in dynamic traitor tracing schemes [5], as well as in schemes that trace history recording and abrupt receivers [6]. In such systems, tracing will succeed even if the pirate DECODE_ORACLEr takes protective measures (for example, shuts down) when it detects tracing or is remotely accessible.
Another set of important techniques involves information hiding [7]. Watermarking and fingerprinting allow the embedding of digital marks into a file that are resilient to removal. Watermarking personalizes the file to its owner and can be used to claim ownership. Fingerprinting, on the other hand, personalizes the file to its licensee to trace his or her identity in case of redistribution.
Regarding the implementation of a DCD system, software obfuscation methods [8] are of particular interest since hiding the internals of a DCD system improves system robustness. Obfuscated code is difficult to reverse-engineer, discouraging tampering with the reproduction device of a DCD system. A reproduction device with obfuscated code that is installed on a computer, if it is combined with other tamper-resistance techniques, can provide highly flexible licensing schemes.
Finally, cryptographic primitives that provide privacy, such as group signatures [9], will also play a role in the DCD context. Digital content consumption may reveal sensitive personal information whose unauthorized usage may hurt the content consumer. In particular, using a group signature scheme, it is possible for a consumer to convince a server that he or she has a valid subscription or that he or she possesses a suitable execution environment without revealing any other identifying information.
In the example of an Internet-based video streaming service, advanced cryptographic mechanisms can make it more robust against adversarial activity. For example, to prevent unauthorized content reception, the packaging mechanism for subscribers can be based on broadcast encryption with a traitor tracing mechanism, which allows the identification of compromised keys and their revocation from the system's transmissions. Watermarking can protect against ownership hijacking. Fingerprinting methods, coupled with dynamic traitor tracing, will protect against unauthorized online redistribution of streams. Anonymity primitives can protect users' selection and streaming patterns from being profiled without their consent and can be used to ensure that a local environment has not been compromised, without sacrificing user privacy. Finally, software obfuscation and tamper resistance techniques can be used to ensure that the internals of the player subsystem are difficult to reverse-engineer or compromise.
4. Conclusion
Cryptographic tools can be instrumental in building effective DRM systems. Still, these tools are far from being fully investigated. Many of the cryptographic primitives mentioned above currently incur substantial communication and computational costs. Even worse, some of the primitives have been proven unattainable in the general case, and suitable special cases need to be identified. For example, while software obfuscation methods do not apply to arbitrary code, it is expected that there are special categories of programs for which obfuscators can be developed.
While the DRM problem goes beyond cryptography, cryptography remains at the very center of the DRM problem, just as good algorithms are at the heart of building successful computer systems. Developing new and more efficient cryptographic primitives suited for DRM systems is one of the major challenges of cryptography today.
With the help of cryptography, we are moving toward reliable DCD systems. Such systems, when combined with proper implementation and development, suitable business models, and legal, ethical, and social frameworks, will provide the viable DRM solutions of the future. In ten or 20 years, the DRM landscape will be shaped in ways that are impossible to fully predict now. It has even been argued that DRM can become the platform over which a nightmarish Orwellian cyber future will unfold, where certain contents will be reserved for the “elite” and withheld from the masses [10].
Will DRM make access to knowledge the privilege of the few while consigning the masses to a new dark age? DCD systems are a new and exciting technology, and society needs time to mature in understanding their capabilities and limitations as well as to develop appropriate ethical and economic frameworks around their use. Technology alone cannot be blamed for being used to our detriment. As citizens of the emerging electronic society, we have the responsibility of ultimately determining how intellectual content will be distributed via the information highway.
Table 1: Cryptographic terms
|
TERM |
DEFINITION |
Asymmetric traitor tracing schemes |
Traitor tracing schemes where the traceability mechanism also provides legally admissible evidence of the implication of traitors in a piracy incident. |
Broadcast encryption schemes |
Encryption systems that allow the revocation of compromised keys. |
| Eavesdropping |
Obtaining a copy of the contents of a file without possessing the original (for example, during its transmission). |
Fingerprinting |
The embedding of digital marks into a file that are resilient to removal, to personalize the file to its licensee and trace his or her identity in case of redistribution. |
Group signature |
A special-purpose digital signature allowing people to prove membership to a group while remaining anonymous. |
Illegal content reception |
Consuming content without having a license for it. |
Illegal content redistribution |
Obtaining a legal license to consume content, and then redistributing the content to others in violation of the license. |
| Key |
A string provided to the consumer that allows him or her to decrypt and consume contents. |
| Key leakage |
The act of transferring a key by a consumer (also known as a “traitor”) to a pirate. |
| License |
A contract between content producers and consumers. |
Ownership hijacking |
Unlawfully taking over the ownership of digital content and using it as one’s own. |
Software obfuscation |
Scrambling of executable code so it runs, but cannot be reverse-engineered to its source code. |
Traitor tracing schemes |
Encryption systems that provide protection against key leakage by enabling the server to identify pirate keys. |
Watermarking |
The embedding of digital marks into a file that personalize the file to its owner, and can be used to claim ownership. |
| |
| |
Created: Jul 19 2005
Last updated: Jun 15 2007 |
|
 |
| |
Web pages
Digital Millennium Copyright Act (DMCA): the full text of the DMCA (U.S. Public Law 105-304)
Digital WatermarkingWorld: a nonprofit forum on digital watermarking for scientists, researchers, and companies
DRM News Blog: a news site dedicated to informing readers about digital rights management issues
Microsoft Windows Media DRM: Microsoft’s home page for the Windows Media digital rights management (DRM)
USACM Weblog on Intellectual Property: a Weblog for the US Public Policy Committee of the Association for Computing Machinery (USACM) that highlights US intellectual property issues
USACM Policy Brief on DRM: a brief description of USACM’s stance on DRM issues, and a list of USACM’s activities in the DRM area
Articles
Dynamic traitor tracing Fiat, A., Tassa, T. CRYPTO '99.
Group signatures Chaum, D., van Heyst, E. EUROCRYPT ’91
On crafty pirates and foxy tracers Kiayias, A., Yung, M. DRM ‘01
Reconfigurable hardware solutions for the digital rights management of digital cinema Rouvroy, G., Standaert, F.-X., Lefebvre, F., Quisquater, J.-J., Macq, B., Legat, J.-D. DRM ‘04
Revocation and tracing for stateless receivers Naor, D., Naor, M., Lotspiech, J. CRYPTO ‘01
Scalable public-key tracing and revoking. Y. Dodis, N. Fazio, A. Kiayias, M. Yung,
Distributed Computing, Vol. 17, Issue 4, May 2005, pp. 323-347.
The digital imprimatur: how big brother and big media can put the Internet genie back in the bottle Walker, J. Knowledge, Technology, & Policy
The IP war: apocalypse or revolution? Gal, T., Singer, H.M., Popkin, L. DRM ‘03
The right to read Stallman, R. Communications of the ACM
Watermarking, tamper-proofing, and obfuscation - tools for software protection Collberg, C.S., Thomborson, C.D. IEEE Transactions on Software Engineering
Books
Information hiding techniques for steganography and digital watermarking. Katzenbeisser, S., Petitcolas, F.A.P. (Eds.), 1999.
Conferences
ACM Workshop on Digital Rights Management: an annual specialized workshop sponsored by the Association for Computing Machinery (ACM) that is dedicated to DRM research
International Conference on Digital Rights Management: Technology, Issues, Challenges and Systems: a new conference that will serve as a broad multi-disciplinary forum for all DRM-related issues
Reviews
Digital rights management Hilts P. In The Columbia guide to digital publishing, 2003
Digital rights management: technological, economic, and legal and political aspects Becker E., Rump N., Günnewig D., Buhse W., 2003
First principles of copyright for DRM design Camp L. IEEE Internet Computing 7(3): 59-65, 2003
How DRM-based content delivery systems disrupt expectations of "personal use" Mulligan D., Han J., Burstein A. Digital rights management, Washington, DC, USA, Oct 2003, pp. 77-89.
Making money selling content that others are giving away Karp A. CACM 46(1): 21-22, 2003
|
|
 |
|